Cybersecurity Law Report: Ten Cybersecurity Resolutions for Financial Services Firms in 2023
January 11, 2023
Companies in the financial services sector are a natural target for hackers given the value and nature of the data they manage. Faced with this threat, there are a number of steps firms can take to mitigate risk.
In this article for Cybersecurity Law Report, Drawbridge President Jason Elmer shares his input on how companies can improve their cyber defenses in 2023.
Read the full article here
Cybersecurity Awareness Month: ‘See Yourself in Cyber’
October 13, 2022
Accelerate and Enhance Your CyberSecurity and Risk Management Program
By Simon Eyre, Drawbridge CISO
As Cybersecurity Awareness Month 2022 is in full swing, it’s an ideal time for businesses to review their cybersecurity, business continuity and risk management processes. These types of annual events are an easy point in the calendar where companies can take stock of their efforts and engage in wider conversations across the industry to buttress cybersecurity awareness.
This year’s theme, ‘See Yourself in Cyber’, is rooted in the personal. This is a chance to focus on the human elements of cybersecurity and business continuity, from collaboration to cyber hygiene and personal safety online. Drawing on the expertise of the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA), this year’s program will tackle key issues including the skills gap in the cyber sphere, how each individual can be part of the solutions and action points for individuals.
Great Regulatory Expectations
All firms in the alternative investment sector are connected not only to the financial services industry, but also a complex, wide network of partners and customers globally and across different industries. It’s why enhancing private equity and hedge fund cybersecurity programs is crucial. A criminal can successfully disrupt a firm’s business continuity and penetrate defenses by first targeting a portfolio company, partner or third-party vendor. Beyond this, firms can also fall victim to a cyber-attack even if they’re not the intended target but are simply caught in a malware fallout. This interconnectedness – and the potential web of damage – is a major focus for key bodies and regulators.
In February, the SEC proposed changes to how registered investment advisers, registered investment companies and funds handle cybersecurity risk management. The changes are designed to better protect investors and maintain an orderly market, and will be under final action in April 2023. Shortly after in June, we had the findings of the annual Cybersecurity and Financial System Resilience Report published by the Federal Reserve System. The measures detailed include a new cybersecurity training plan that was put into place for Federal Reserve cybersecurity examiners in 2022 and its participation in “one-day, simulated exercises aimed at improving responses to a range of cyber-threat scenarios within the U.S. financial sector.” Across the Atlantic, UK regulators have also proposed legislation to improve the nation’s cyber resilience.
But firms should not wait for regulatory guidance to create and improve their own cybersecurity and risk management programs. After all, criminals won’t wait to attack and disrupt your operations.
Be an Active Participant, Not a Passive Victim
Inactivity is dangerous. Being a key player in the fight against cybercrime does not depend on a firm’s size, number of clients or geography. In fact, all firms in the financial services industry can defend against – and defeat – cybercriminals with a simple formula of commitment, collaboration and trust.
To be a part of the solution, companies must first have a clear commitment to cybersecurity, business continuity and operational resilience. Second, they should demand the same from each vendor, partner and organization in their network (regardless of its size or industry) to reduce vulnerabilities. And third, companies need to have confidence that customers, partners and vendors will share relevant risk information as required.
If alternative investment firms only work with companies that share the same level of commitment to cybersecurity and risk management, they can have greater confidence in their ability to operate safely. And by communicating their cybersecurity expectations and setting standards, they will position themselves as a reliable partner.
Call it safety in numbers. This shared obligation to cybersecurity creates a virtual battalion of companies standing shoulder to shoulder to defend against skilled and sophisticated cybercriminals. And that’s how companies move beyond simply deploying solutions to fight cybercrime – to becoming part of the solution themselves.
Simon Eyre is Chief Information Security Officer at Drawbridge. As a trusted private equity and hedge fund cyber security partner and industry leader in financial services cybersecurity, Drawbridge helps firms build holistic, robust cyber security and risk management programs that combat vulnerabilities before they cause business disruptions.
Connect with our team to find out how Drawbridge can build and strengthen your company’s defenses and improve your business continuity and operational resilience.
Cyber Alert: Apple Security Flaw Actively Exploited
August 19, 2022
Read on for more information and resources for protecting yourself and your devices.
Apple has advised users of iPhone, iPad, and Mac hardware to update their software as soon as possible to protect against vulnerabilities that may grant an attacker complete control of these devices.
These security flaws affect iOS, iPadOS, and macOS Monterey devices. Apple has stated that “An application may be able to execute arbitrary code with kernel privileges” which may grant an attacker complete control of the affected device. Because of the significant impact of these exploits, Drawbridge recommends that users of these devices update their software immediately.
How to Protect Yourself:
- Update iOS and iPad OS to versions 15.6.1
- Update macOS Monterey 12 to 12.5.1
- If you’re running macOS 10 Big Sur or mac OS 11 Catalina, update to Safari 15.6.1 and keep an eye out for future OS updates
Technical Details:
Attackers may be able to exploit these vulnerabilities by tricking someone into accessing a web page which hosts malicious code. They can then leverage these vulnerabilities to execute this code on the victim’s device with kernel level privileges, which means that the attacker can run this code with unrestricted access rights. Relevant CVEs have been outlined below:
- CVE-2022-32893: A site hosting malicious content can trick iPhones, iPads and Macs into running unauthorized and untrusted software code.
- CVE-2022-32894: An attacker who has exploited the above vulnerability will be able to leverage CVE-2022-32894 to take over the operating system kernel, gaining administrative control of the device.
General Best Practices & References:
- Ensure devices are updated regularly.
- Avoid suspicious websites
- Follow the principle of least privilege when assigning permissions to accounts on macOS devices running older operating systems
Cybersecurity Alert: Authentication Vendor Okta Suffers Breach
March 23, 2022
Identity provider Okta was the victim of a breach perpetrated by a hacking group known as Lapsus$. The impact and extent of the breach are still being investigated; however, several details have been released:
- The attacker had access to an Okta engineer’s laptop for five days, though the service itself had not been breached and is still fully functional.
- The impact appears to be limited to the ability to reset passwords and MFA factors. Investigation into the full impact of the breach is ongoing.
- Okta has stated that the attackers would not have access to customer passwords or user databases.
In a statement issued by Okta, they noted that 2.5% of their customers may have had their data viewed or acted upon. These customers have been contacted directly.
While the investigation is unfolding, Drawbridge recommends that Okta customers take precautionary measures to ensure their Okta environment is as secure as possible.
Cybersecurity Alert: White House Highlights Elevated Cybersecurity Threat
March 22, 2022
Earlier this week, U.S. President Joe Biden warned of the increased threat of Russian cyber attacks in response to sweeping sanctions. As the conflict in Ukraine continues, state-sponsored attacks on NATO members and allies are growing in likelihood, and private businesses are also at risk of being targeted.
In a statement released by The White House, President Biden “urge[d] our private sector partners to harden your cyber defenses immediately.”
As is often the case, there is no firm intelligence of an imminent attack, so it is impossible to warn a certain firm, sector, or governmental body to take specific actions at this time. However, considering past patterns of both state-sponsored and other attacks, it is advisable for all firms to harden their defenses immediately. Drawbridge believes this elevated threat is of particular urgency and concern for our clients in the financial sector and we advise immediate preparatory actions.
To better protect yourself and your organization, we highlight the following points from the White House alert and associated fact sheet:
- Mandate the use of multi-factor authentication on your systems to make it harder for attackers to get onto your system.
- Check with your cybersecurity professionals to make sure that your systems are patched and protected against all known vulnerabilities.
- Run exercises and drill your emergency plans so that you are prepared to respond quickly to minimize the impact of any attack.
- Educate your employees to common tactics that attackers will use over email or through websites, and encourage them to report if their computers or phones have shown unusual behavior, such as crashing or operating very slowly.
Further, we recommend these additional actions to reinforce your cybersecurity posture:
- Avoid clicking links for news or information about the war from unknown sources, particularly on social media like Twitter and Reddit. If you cannot read the link or preview, it is not advisable to click—now more than ever.
- Avoid government websites for Ukraine or Russia unless you are confident on the destinations of your web links and require their diplomatic services. These sites may be targeted more than others and visiting them, unless absolutely necessary, could pose unique risks.
- Take particular care with supply chain/third-party risks, outsourced software development, and plug-ins to SaaS services such as Slack, Teams, Trello, and Salesforce. If you haven’t performed cybersecurity risk assessments on such services, now is the time to review their origin and cybersecurity measures.
Cybersecurity News: The Impacts of Cryptocurrency on Cybersecurity Within Your Firm
January 13, 2022
A cryptocurrency is a digital asset that operates as a medium of exchange.
It can be used to make electronic payments, and utilizes a form of cryptography in order to secure payments, as well as a distributed, immutable ledger for tracking ownership and transactions. As the popularity of cryptocurrencies continues to expand, questions linger as to both their sustainability, as well as how to defend from potential breaches through crypto platforms.
Firms dealing with cryptocurrencies, or considering getting involved, should be wary of their adoption without the right protocols in place. As cyber threats are on the rise worldwide, these same threats extend to cryptocurrencies, with malicious parties seeking to find the gaps between security and your firm, emboldened by the anonymity and decentralized nature of cryptocurrencies.
Generally, governments and federal regulators are playing catch-up as to how to treat cryptocurrency. Because of this, cybercriminals have benefited greatly, and have been able to take advantage of openings in existing security structures. In a typical attack on crypto assets, malicious parties are able to hack into trading platforms and steal funds. This breach can potentially lead to the theft of both significant financial holdings and personal information, and can affect other areas of your firm.
A particular trend in recent years has been that of ransomware. With ransomware, malicious parties can hide their identities, and ask for ransom of private information or assets in the form of cryptocurrencies. Typically, this is a form of cybercrime where the attackers are unable to be traced due to the nature of cryptocurrencies.
The best way to protect your firm from cybercrime of any kind is by implementing proper cybersecurity protocols and practices. The expert cybersecurity team at Drawbridge can help with this every step of the way. Drawbridge’s unique software allows your firm to manage various facets of your cybersecurity program on a single platform, reducing the complexity and expense of managing multiple tools and relationships. Drawbridge’s vulnerability management capabilities locate and mitigate potential breaches with ease, while continuous network scanning, vendor due diligence, and—coming soon—dark web monitoring tools round out your firm’s readiness.
Contact Drawbridge today to schedule a demo, and learn how your cybersecurity needs can be met.
Cybersecurity News: What the TSAs New Railway Cybersecurity Mandates Mean
October 15, 2021
As looming cybersecurity threats continue throughout the nation, the need for federal bodies and private industries to heighten cybersecurity regulations has never been greater.
In preparing certain sectors for potential breaches, the federal government hopes that they can be more prepared and efficient in dealing with cyber-attacks
Recently, the Transportation Security Administration (TSA) has imposed new cybersecurity mandates on the aviation and railway industries, instructing business within these industries to strengthen cybersecurity and to meet incoming regulations.
A major aspect of this mandate as it pertains to the railway industry is the need to appoint official cyber chiefs. The goal is for businesses within this industry to draft recovery plans, as well as to meet new regulatory requirements.
This mandate has been implemented in an effort to mitigate growing concerns over both the railway and aviation industry’s cybersecurity preparedness. Of the potential threats that face these industries, that of ransomware has been highlighted as a major concern.
Ransomware targets vulnerable parties, holding private information or assets hostage at the cost of a ransom. To avoid these breaches in the future, robust cybersecurity measures must be implemented.
The TSA have specifically targeted high-risk members of the railroad and aviation industries with the goal of putting together further cybersecurity plans. The hope is that with a combination of regulatory readiness and an emphasis on cybersecurity focus, the threat of ransomware and other potential cyberattacks on these fundamental industries can be reduced.
Drawbridge is a premier provider of cybersecurity software and solutions and a trusted partner to more than 300 funds in the alternative investment industry with more than $800 billion in Assets Under Management. Our technology platform empowers firms to build customized cyber programs that proactively manage vulnerabilities, simplify risk management and grow with their business.
For those firms seeking the best possible defense from these worldwide growing threats, schedule a demo with Drawbridge today to learn how your cybersecurity needs can be met!
Cybersecurity News: The White House’s New Emphasis on Cybersecurity Jobs
October 1, 2021
Throughout the global pandemic, multiple cybersecurity breaches have made headlines for the brazen and large-scale nature of these attacks.
Following these events, cybersecurity has been brought further into public light. This is certainly true of federal bodies, which have indicated a need for the heightening of cybersecurity procedures throughout the United States.
Ransomware has also played a role in publicized cyber-attacks recently. New technologies have allowed malicious parties to more easily utilize ransomware, and because of this more and more firms are at risk.
This is not to mention the threat to public safety, as government agencies are also seeing an uptick in the amount of potential breaches they face. It has become clear to governments worldwide that cybersecurity must become a major facet of defense moving forward. The White House has responded with various new methods to approach this cyber-defense issue.
Firstly, as part of an executive order originally given in May, the federal government has been tasked with reevaluating previous softwares and security tools used by agencies. This is a significant step forward, as security tools utilized by agencies may not have been properly scrutinized in the past.
Major technology companies have also pledged large investments that are meant to accelerate cybersecurity advancements across the board, for the nation and for privately run companies. A major emphasis was also placed on multifactor authentication as a simple yet effective method for mitigating simple breaches.
As for further outlined policy points, emphasis has been placed on cybersecurity experts, their training, and nurturing. In a world of heightened cyber-risk, there must be a sufficient number of professionals to meet this new challenge. Through expansions of private firms and technology giants in the hiring and training of a cybersecurity workforce that is larger than ever, the hope is that threats like ransomware and other cyber-attacks can be limited.
More on the May executive order can be found on The White House website.
Security professions that your firm can trust are not easy to come by. However, Drawbridge’s expert team is well-equipped to face the ever-changing future of cybersecurity. Schedule a demo with Drawbridge today to learn how your cybersecurity needs can be met.
Cybersecurity News Cycle: White House Briefing Details National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems
August 6, 2021
On account of increasing and strengthening cybersecurity threats, President Biden and his administration have released a National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems.
The memorandum details a number of measures to be taken by the administration to mitigate cyber attacks for critical infrastructure control systems and keep them protected.
“Protection of our Nation’s critical infrastructure is a responsibility of the government at the Federal, State, local, Tribal, and territorial levels and of the owners and operators of that infrastructure… The degradation, destruction, or malfunction of systems that control this infrastructure could cause significant harm to the national and economic security of the United States,” said President Biden in the memorandum.
The memorandum brings forward five sections of action to be taken by President Biden and his administration. Section 1 details policy to “safeguard the critical infrastructure of the Nation, with a particular focus on the cybersecurity and resilience of systems supporting National Critical Functions.”
Section 2 details the Industrial Control Systems Cybersecurity Initiative, a “voluntary, collaborative effort between the Federal Government and the critical infrastructure community to significantly improve the cybersecurity of these critical systems.” Section 3 looks to further the initiative, with efforts to build on, expand, and accelerate ongoing cybersecurity efforts in critical infrastructure sectors as an important step in addressing these threats.
Section 4 goes over the need for critical infrastructure cybersecurity performance goals, as a “need for baseline cybersecurity goals that are consistent across all critical infrastructure sectors, as well as a need for security controls for select critical infrastructure that is dependent on control systems” increases.
Lastly, Section 5 details that the memorandum will operate without impacting several factors.
“ICS is particularly challenging where cybersecurity is concerned. Historically “availability” from the CIA Triad (Confidentiality, Integrity, Availability) features higher on the priority list than in traditional IT. Industrial Control Systems and Operational Technology often utilize older legacy tech, which compounds the difficulty in deploying modern cybersecurity monitoring platforms,” said Simon Eyre, Chief Information Security Officer of Drawbridge.
“Companies may even struggle to find the right skills to offer software patches to these older systems. This ‘Call to Arms’ by the Biden administration may be just the ticket critical infrastructure needs to gain the funds and overcome these challenges,” he added.
With increasing cyber threats, it’s imperative to stay up to date with important information like the memorandum above. To read the full National Security Memorandum, click here.
Cybersecurity News Cycle: The Absolute 2021 Endpoint Risk Report is Released
July 22, 2021
The third annual edition of Absolute’s Endpoint Risk Report has been released.
This year’s report examines where organizations should be focusing their efforts as they continue to support new ways of working amidst a fast-evolving cyber threat landscape.
In their report summary, Absolute says the following:
“The rapid shift to support new ways of working challenged even the most sophisticated organizations to maintain healthy security postures. Amidst an ever-evolving threat landscape, IT and security teams raced to adopt risk management strategies for environments that would have been unimaginable only two years ago.
“Investment in cybersecurity technologies reached new heights but was outpaced by the increase in data breaches — and the average cost of a breach was significantly higher for organizations with remote teams.
“With 73% of respondents in a recent CSO study saying that the impact of the pandemic will alter the way their business evaluates risk for at least the next five years,3 the third annual edition of Absolute’s Endpoint Risk Report sets out to understand where organizations should focus their efforts now.”
The report examines numerous factors, such as remaining vulnerabilities, the increase of sensitive data on devices, endpoint complexity exacerbating risks, strategies to reduce risk, and much more. Click here to read the full report and gain a better understanding of what your business can do to reduce cyber risks and stay protected in the face of the evolving cyberthreat landscape.
Cybersecurity News Cycle: The Kaseya Cyber Attack Compromises the Security of Up to 1,500 Businesses
July 19, 2021
There is growing evidence that cyber attackers are only becoming stronger and better at what they do.
As the cybersecurity landscape evolves to meet these new challenges, so do hackers, who evolve their own cyber threats and attacks.
Last week’s Kaseya cyber attack compromised the security of around 1,500 businesses and organizations globally, including the New Zealand school district we covered in last week’s blog post.
According to a report by NPR, “The attackers found a vulnerability in the product of Kaseya, a U.S.-headquartered company that provides software tools to its clients — IT outsourcing companies — which in turn provide services to their clients…Hackers have demanded $70 million in cryptocurrency in exchange for a key that decrypts all of the victims’ data.”
The group claiming responsibility for the attack is none other than REvil, the group that was responsible for the ransomware attack on meat processor JBS in May.
It’s important to be diligent about your cybersecurity program and understand the constant changes. Drawbridge specializes in understanding and responding to the evolving cybersecurity landscape, and helping you maintain and adapt your cybersecurity program to tackle new and existing threats.
Cybersecurity News Cycle: Mortgage Lender First American charged for Inadequate Action in Cybersecurity Vulnerability Breach
June 23, 2021
Making sure your business is protected from cyber threats can be a daunting task to take on.
With so many factors involved, it can be difficult to know where to start. At Drawbridge, we have all the tools to keep you protected from cyber threats and keep your company’s data safe. With services like Cybersecurity Training, Vulnerability Management and much more, Drawbridge is fully equipped and ready to help you keep your business secure.
Cyberthreats are everywhere, and no business, organization or firm is an exception to these risks, no matter how big or small. In recent news, one of the largest mortgage lenders in the country, First American, has been charged by the Securities and Exchange Commission (SEC) for inadequate cybersecurity practices.
First American failed to protect the personal information of its customers, or inform customers of the extent of a serious data breach the mortgage lender withstood. Its failure to mitigate the breach and take appropriate measures to keep customers informed and follow proper incident response is what put First American in the line of fire.
According to an report by Illinois News Today, “First American issued a statement in response to the leak the same day it was notified of the leak, but according to the SEC, that alone was not a sufficient response plan. According to official orders, the company’s senior management has learned that information security personnel haven’t identified the leak a few months ago and haven’t fixed the problem, made a response plan, or informed anyone. It wasn’t done. The SEC claimed that this inadequate cyber incident response put personal information at risk.”
According to a press release by SEC, on account of the Exchange Law Rule 13a, First American agreed to pay a cease and desist order and a $487,616 fine. First American did not confirm or deny the SEC’s findings, but complied with the settlement agreement.
Understanding cyber threats and mishaps like the one above and knowing the best method of action to protect against them isn’t always easy. Drawbridge is ready and willing to assess your situation, adapt your current cybersecurity strategy, and customize our approach to protect you most effectively. Contact us today to get started.
CYBERSECURITY NEWS: SEC Observations
January 27, 2020
SEC OCIE Publishes Observations on Cybersecurity and Resiliency Practices
On Monday, January 27th, 2020, the U.S. Securities and Exchange Commission’s Office of Compliance Inspections and Examinations (OCIE) issued examination observations related to cybersecurity and operational resiliency practices.
The observations focus on the following areas:
- Governance and Risk Management
- Access Rights and Controls
- Data Loss Prevention
- Mobile Security
- Vulnerability Management
- Incident Response and Resiliency
- Vendor Management
- Training and Awareness
In conclusion, the OCIE encourages all covered entities to review cyber practices, policies and procedures. The OCIE will continue to assess the level of preparedness of these entities and believes that implementing policies, controls, and solutions pertaining to the items noted in the report will make organizations more secure. Cybersecurity remains a prominent focus area of the SEC, and the OCIE will continue working with organizations to identify and address cybersecurity risks.
For additional information, please visit:
https://www.sec.gov/news/press-release/2020-20
Cybersecurity News: SEC & CFTC Update
January 8, 2020
2020 SEC EXAMINATION PRIORITIES
On Tuesday, January 7th, 2020, the U.S. Securities and Exchange Commission (SEC) released the examination priorities for 2020. The SEC has shifted their examination priorities from years past in an effort to adapt to emerging risks, but cybersecurity continues to remain a top priority for the SEC. The SEC will be focusing on the following key areas with respect to cybersecurity:
- Proper configuration of network storage devices
- Information security governance
- Retail trading information security
- Governance and risk management
- Access controls
- Data loss prevention
- Vendor management (this includes cloud-based service providers)
- Training
- Incident response and resiliency
- Proper disposal of retired hardware
- Controls surrounding online access and mobile application access to customer brokerage account information
There will be a renewed focus on S-ID (Identity Theft Red Flags Rules) and S-P (Privacy Rules), which requires SEC-regulated entities to implement policies and procedures designed to do the following:
- S-ID
- Identify identity theft red flags
- Detect the existence of those red flags
- Respond appropriately to the detected red flags
- Periodically assess and update the identity theft program
- S-P
- Adopt written policies and procedures that address administrative, technical, and physical safeguards for the protection of customer records and information
For additional information, please visit: https://www.sec.gov/news/press-release/2020-4.
CFTC WARNS REGISTRANTS OF THREATS AND REQUESTS INFORMATION
On December 30th, 2019, The Wall Street Journal published an article outlining a sustained cyberattack against cloud service providers by a Chinese hacker group known as APT10. By design, cloud service providers operate by sharing infrastructure and resources between many clients. This type of design makes them a valuable target, as a provider with inadequate cybersecurity controls may open themselves and their clients up to attack from malicious actors.
CFTC Cyber Threat Alerts
- On January 3, 2020, the Commodity Futures Trading Commission (CFTC) issued two cyber threat alerts centered around the hacking of the cloud service providers described in the WSJ article.
- Swap Dealers (SDs), Futures Commission Merchants (FCMs) should respond to the alert they received from the Division of Swap Dealer and Intermediary Oversight (DSIO) by January 10, 2020, on whether or not any of their cloud service providers were affected by the attack.
- Commodity Pool Operators (CPOs), Commodity Trading Advisors (CTAs), Introducing Brokers (IBs) and Retail Foreign Exchange Dealers (RFEDs) should respond to the alert they received from the National Futures Association (NFA) by January 10, 2020, only if any of their cloud service providers were affected by the attack. These registrants DO NOT need to respond if they were not affected.
- Any registrant whose cloud service providers have been affected by the attack should include a summary of the information it has gathered, and its plan to protect its systems and data.
- All CFTC registrants should respond by January 20, 2020, on whether or not it has received communications from any third parties regarding the attack or a related potential cyber event. DSIO is requesting responses from all of its registrants.
What is Cloud Hopper?
- Operation Cloud Hopper represents a series of continuous attacks against cloud service providers and their clients by Chinese hacker group APT10.
- The goal of these attacks was to gain access to sensitive intellectual and customer data. Once the attackers gained access to a cloud service provider, they used the shared cloud infrastructure to “hop” from one target to another, gaining access to sensitive data.
How did this attack occur, and who is affected?
- Attackers used phishing emails to compromise employee accounts, while also using network infiltration tools to circumvent various security controls.
- Compromised credentials were leveraged to bypass security borders, successfully using cloud service providers as an attack vector to gain access to corporate data of multiple organizations.
- Reporting is still coming in regarding the major companies that were affected, but we do know cloud providers such as Hewlett Packard Enterprise, IBM, and CGI Group in Canada were all victims.
- The scope of the attack and amount of compromised data is still unknown, and the attack appears to be ongoing.
How do I protect myself?
- Understand where your sensitive data is stored. This will help you configure targeted security solutions for your most critical data.
- Conduct vendor due diligence on a yearly basis. Your vendors are an access point to your data, and they should be continuously maintaining and improving their security posture as threats evolve.
- Document and consistently enforce policies and controls. Human error is the most common target of cyberattacks. Security policies require users to act in a security-focused manner, and technical controls act as a safety net when human error occurs.
- Implement strict account management practices. Accounts should be monitored and reviewed on a regular basis to ensure correct privileges and usage. Accounts are less likely to be compromised if they are tracked and maintained.
- Institute robust monitoring controls. Monitoring your network, accounts, and data allows you to detect and remediate a cyberattack quickly and efficiently. Many cloud providers make monitoring and alerting tools available to their clients, and we recommend that you have a discussion with your vendors around these controls.
- Review your contracts with vendors for breach notification language.
- Formalize change controls. Changes to permissions, accounts, or network controls should be reviewed, authorized, and documented. Awareness of the changes occurring in your network or within your cloud tenant will reduce the risk of compromise due to unnoticed modifications.
- Encrypt data at rest. Most cloud providers offer encryption at rest; however, you should verify that this is the case with any cloud provider storing your data.
For additional information, please visit: https://www.wsj.com/articles/ghosts-in-the-clouds-inside-chinas-major-corporate-hack-11577729061.
CYBERSECURITY RISK ALERT: WhatsApp Vulnerability
May 14, 2019
To update WhatsApp on various platforms:
- Android: Go to Play Store, then tap Menu > My apps & games. Tap UPDATE next to WhatsApp Messenger.
- Alternatively, go to Play Store and search for WhatsApp. Tap UPDATE under WhatsApp Messenger.
- iPhone: Go to App Store, then tap Updates. Tap UPDATE next to WhatsApp Messenger.
- Alternatively, go to App Store and search for WhatsApp. Tap UPDATE next to WhatsApp Messenger.
- Windows Phone 8.1: Go to Store, then tap Menu > my apps > WhatsApp > update.
- Alternatively, go to Store and search for WhatsApp. Tap WhatsApp > update.
- Windows Phone 10: Go to Microsoft Store, then tap Menu > My Library. Tap Update next to WhatsApp.
- Alternatively, go to Microsoft Store and search for WhatsApp. Tap WhatsApp > Update.
- KaiOS: Press JioStore or Store on the apps menu. Scroll to the side to select Social, then select WhatsApp. Press OK or SELECT > UPDATE.
For additional information, please visit: https://www.facebook.com/security/advisories/cve-2019-3568
& https://www.dataprotection.ie/en/news-media/press-releases/dpc-statement-whatsapp-security-incident
CYBERSECURITY RISK ALERT: Broadcom Wi-Fi
April 18, 2019
For individuals using Broadcom Wi-Fi, on April 17, 2019, the CERT Coordination Center (“CERT/CC”) published information identifying various vulnerabilities stemming from the Broadcom ‘w1’ driver and open source ‘brcmfmac’ driver for Broadcom Wi-Fi chipsets. Ultimately, these vulnerabilities could allow an unauthenticated attacker to execute arbitrary code on a vulnerable system, most frequently resulting in a denial-of-service (DoS) attack.
Patches have not been made available for the ‘w1’ driver. Until patches become available, a workaround is to connect exclusively to trusted Wi-Fi networks. Drawbridge will continue to monitor the issue.
For additional information, please visit: https://www.kb.cert.org/vuls/id/166939/.
CYBERSECURITY RISK ALERT: SEC Regulation S-P Risk Alert
April 16, 2019
Today, April 16, 2019, the SEC’s Office of Compliance Inspections and Examinations (OCIE) published a risk alert regarding compliance issues related to Regulation S-P. The focal points identified by the OCIE were the failure to provide customers with privacy and opt-out notices, as well as the failure to adopt written policies and procedures that address administrative, technical, and physical safeguards for the protection of customer records and information.
The OCIE also commented on the lack of sufficient safeguards despite having written policies and procedures were in place. Among the common areas of insufficiency were:
- Policies and procedures failing to address safeguards for customer PII on personal devices
- Electronic communications
- Insufficient training is being provided and firms are failing to monitor employee compliance with policies
- Failing to prohibit employees from sending and receiving customer PII using unsecure networks
- Failing to sufficiently manage PII held by third-party vendors
- PII inventory being insufficiently monitored and maintained
- Incident response plans that aren’t addressing important areas
- Customer PII being stored in unsecure physical locations
- Misuse or mishandling of customer login credentials
- Departed employees maintaining access to firm systems and customer information after departure
RISK ALERT: GOOGLE CHROME VULNERABILITY
March 8, 2019
Recently, Google identified a zero-day vulnerability affecting Chrome internet browsers. The vulnerability is a memory management error which could allow a remote attacker to read the contents of files stored on a user’s computer. Google addressed the vulnerability in Chrome version 72.0.3626.121.
Check if your Chrome browser is up-to-date:
- Click this icon in the upper right corner of your browser;
- Go to ‘Help’;
- Go to ‘About Google Chrome’;
- Ensure that your browser displays version 72.0.3626.121
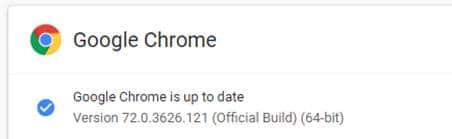
If your browser is not up-to-date, update it immediately.
For additional information, please visit: https://chromereleases.googleblog.com/2019/03/stable-channel-update-for-desktop.html
CYBERSECURITY RISK ALERT: CISCO WEBEX VULNERABILITY
March 1, 2019
Cisco has identified a vulnerability in its Webex Meetings Desktop App and Webex Productivity Tools. By invoking the update service command with a crafted argument, an authenticated, local attacker could run arbitrary commands with SYSTEM level user privileges. The vulnerability may also be exploited remotely in Active Directory deployments by leveraging operating system remote management tools.
Cisco has released the following software updates to remediate the vulnerability:
- Cisco Webex Meetings Desktop App Release 33.6.6 and 33.9.1; and
- Cisco Webex Productivity Tools Release 33.0.7
CYBERSECURITY RISK ALERT: Cisco Webex Alert
February 28, 2019
Cisco Webex Cybersecurity Alert: Cisco has identified a vulnerability in its Webex Meetings Desktop App and Webex Productivity Tools. By invoking the update service command with a crafted argument, an authenticated, local attacker could run arbitrary commands with SYSTEM level user privileges. The vulnerability may also be exploited remotely in Active Directory deployments by leveraging operating system remote management tools.
Cisco has released the following software updates to remediate the vulnerability:
- Cisco Webex Meetings Desktop App Release 33.6.6 and 33.9.1; and
- Cisco Webex Productivity Tools Release 33.0.7
CYBERSECURITY NEWS ALERT: CFTC’s First Ever Examination Priorities
February 26, 2019
On February 12, 2019, the Commodity Futures Trading Commission (CFTC) released its first-ever examination priorities for registrants of the Division of Market Oversight (DMO), Division of Swap Dealer & Intermediary Oversight (DSIO), and Division of Clearing & Risk (DCR). A notable inclusion in the examination priorities is service provider oversight.
In the release, the CFTC also mentions their practice of conducting System Safeguard Exams to assess the risk assessment and cybersecurity testing programs of covered entities. The focus on self-governance, oversight, and sound cybersecurity practices aligns the CFTC’s examination approach with the Securities and Exchange Commission.
For additional information, please visit: https://www.cftc.gov/PressRoom/PressReleases/7869-19
CYBERSECURITY RISK ALERT: Vulnerability
February 13, 2019
Microsoft has recently identified a vulnerability (CVE-2019-0676) within Internet Explorer (IE). When IE improperly handles objects in memory, it is possible for an attacker to test for the presence of files on disk. Attackers can exploit this vulnerability by sending the user a link leading to a malicious website and coercing them to follow the link. This vulnerability affects versions 10 or 11 of IE.
Microsoft has addressed this vulnerability with various patches as of Tuesday 2/12/2019.
For additional information, please visit: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0676#ID0EN
Cybersecurity News Alert: SEC Infiltration EDGAR System Hack
January 16, 2019
On Tuesday, January 15th, the U.S. Securities and Exchange Commission (SEC) announced that it charged nine defendants in an alleged hack of the SEC’s EDGAR system. The hackers allegedly infiltrated the SEC EDGAR system and extracted nonpublic information to use for illegal trading, ultimately profiting $4,135,015 in the process.
The hackers mostly stem from Ukraine and Russia, but two defendants were identified in California. Defendants have been charged with federal securities anti-fraud laws as well as SEC anti-fraud rules and is seeking penalties, return of profits with prejudgment interest, and enjoining the defendants from committing future violations.
For additional information, please visit: https://www.sec.gov/news/press-release/2019-1
Cybersecurity Vulnerability Alert – Microsoft Windows
January 9, 2019
Microsoft Windows Alert: Microsoft has recently identified a vulnerability in its Windows products. The vulnerability could allow a local attacker to elevate privileges on the targeted Windows-based system. A successful attack would require user-level access and would allow the attacker to execute arbitrary code with escalated privileges and compromise the system entirely.
Microsoft has released software updates to address the vulnerability available here: https://bit.ly/2j3EEiA
Cybersecurity Risk Alert – NFA
January 7, 2019
The National Futures Association (NFA) recently amended the NFA Compliance Rules 2-9, 2-36, and 2-49: Information Systems Security Programs. The amendments address three areas originally covered in the 2016 Interpretive Notice and go into effect on April 1, 2019. The amendments are as follows:
- Cybersecurity Training
- Previously, the NFA required employee cybersecurity training upon hire and periodically during employment. With the amendments, training will be required upon hire, at least annually, and more frequently if necessary (e.g. if the employee is the subject of a data breach or has displayed poor cybersecurity practices).
- Amendments also require Member Firms to describe the topics covered during training in their information security policies.
- Information Systems Security Program (ISSP) Approval
- The NFA has determined that ISSP approval by an “executive-level official” of a Member Firm is not uniformly understood. The language has been amended to require ISSP approval by the Member Firm’s “senior-level officer with primary responsibility for information security or another senior official who is a listed principal and has the authority to supervise the Member’s execution of its ISSP.”
- Notice Requirement
- Currently, Member Firms are not required to notify the NFA of cybersecurity incidents. The amendments will now require Member Firms to notify the NFA of a cybersecurity incident if the incident results in the following:
- A loss of customer or counterparty funds or loss of a Member Firm’s capital; or
- Notification of an incident is reported to customers or counterparties pursuant to state or federal law.
- Currently, Member Firms are not required to notify the NFA of cybersecurity incidents. The amendments will now require Member Firms to notify the NFA of a cybersecurity incident if the incident results in the following:
For additional information, please visit: https://www.nfa.futures.org/news/newsNotice.asp?ArticleID=5085
Cybersecurity Vulnerability Alert – Cisco
December 27, 2018
Cisco Cybersecurity Alert:
NOTE: This vulnerability affects Cisco ASA Software that is running on any Cisco product that has web management access enabled.
On December 19th, Cisco identified a vulnerability in the authorization subsystem of ASA Software on Cisco products. This vulnerability would allow an authenticated, but unprivileged, remote attacker to perform privileged actions by using the web management interface, if enabled. The result of an attack could be the unauthorized retrieval of files from the affected device. Cisco has released software to address the vulnerability. An effective workaround is enabling command authorization in Cisco ASA.
Cybersecurity News Alert – Microsoft
December 21, 2018
Microsoft Internet Explorer Alert: On Wednesday, December 19th, Microsoft released a critical security update for Internet Explorer after receiving a report about a new vulnerability being used in targeted attacks. The browser’s vulnerability could allow an attacker to gain the same user rights as the current user. If that user has administrative rights, the attacker could then take control of an affected system and install programs, change or delete data, or create new accounts.
Microsoft’s security update addresses the vulnerability by modifying how the scripting engine handles objects in memory.
According to Microsoft, users who have Windows Update enabled and have applied the latest security updates, are protected automatically. We encourage you to check with your IT Provider or IT Department to ensure patches are applied.
For additional information, please visit: https://bit.ly/2BtfNjE
CYBERSECURITY NEWS ALERT: December 2018
December 20, 2018
On December 20th, the Financial Industry Regulatory Authority (FINRA) released a report detailing the effective cybersecurity practices and common risks observed during recent examinations. The report focused on the following key areas:
- Branch Controls
- Phishing Attacks
- Insider Threats
- Penetration Testing
- Mobile Device Security
Branch Controls: Maintaining rigorous cybersecurity controls is a firm’s best defense against attacks and human error. Establishing policies, controls, and an overall cybersecurity program promotes firm cybersecurity awareness and fosters a “security-first” environment. In this section FINRA reviews:
- Policies and Procedures (Information Security Policy, Incident Response Plan, etc.)
- Asset Inventory
- Third-Party Risk Management
- Technical Controls (Encryption, Strong Passwords, etc.)
- Patch Maintenance
Phishing Attacks: Phishing is one of the most common threats to firms. This section details specific types of phishing (“spear-phishing” and whaling”) as well as controls that FINRA recommends firms should implement in order to combat phishing attacks. In this section FINRA reviews:
- Email and Browser Protection
- Network Security
- Risk Assessments
- Endpoint Malware Protection
Insider Threats: Insider threats remain a major cybersecurity concern for firms. Bad actors who had or may still have authorized access to the firm’s network represent a very present and capable threat to the firm’s network security. Among other methods detailed by FINRA, regularly reviewing access rights is imperative to combating insider threats. In this section FINRA reviews:
- Identity and Access Management (Access Rights and Controls)
- Secure System Configuration
- Data Protection (Encryption, Backup Retention, etc.)
- Security Awareness Training
Penetration Testing: Penetration testing and vulnerability scanning are an important part of a firm’s cybersecurity program. Testing and scanning the firm’s network allows the firm to identify specific deficiencies and target areas for improvement. In this section FINRA reviews:
- Vulnerability Scanning
- Selecting Security Vendors/Due Diligence
Mobile Device Security: Mobile devices are a part of everyday life and, in many cases, essential to a firm’s business and workflow. However, with increased mobility comes increased risk as mobile devices are particularly susceptible to risks like spam, spoofed calls and emails, viruses, etc. Implementing mobile device security controls and establishing a “security-first” approach to mobile device use is essential to mobile device security. In this section FINRA reviews:
- MDM
- Remote wipe
- Password requirements
- Security software on devices
For additional information, please visit: http://www.finra.org/newsroom/2018/finra-publishes-report-selected-cybersecurity-practices-2018
Cybersecurity News Alert – U.S. Securities and Exchange Commission (SEC)
December 20, 2018
SEC Cybersecurity News Alert: On Thursday, December 20th, the U.S. Securities and Exchange Commission (SEC) released the examination priorities for 2019. The SEC has shifted their examination priorities from years past in an effort to adapt to emerging risks, but cybersecurity continues to remain a top priority for the SEC.
The SEC will be focusing on the following key areas with respect to cybersecurity:
- Proper configuration of network storage devices
- Information security governance
- Policies and procedures related to retail trading information security
- Cybersecurity practices at firms with multiple branch offices
- Governance and risk assessment
- Access rights and controls
- Data loss prevention
- Vendor management
- Cybersecurity training
- Incident response planning
For additional information, please visit: https://www.sec.gov/news/press-release/2018-299
Cybersecurity Risk Alert – Facebook
September 25, 2018
Facebook Cybersecurity Risk Alert: On Tuesday, September 25th, Facebook discovered a security breach affecting approximately 50 million users. Attackers exploited a vulnerability in the “View As” feature of Facebook, which allows users to view their profile from the perspective of another user. As a result of the exploit, the attackers stole Facebook access tokens, which could have allowed them to gain control of the user accounts. Access tokens are digital keys that keep users logged in to Facebook and do not require users to re-enter their password every time they use the application.
At this time, it has not been determined whether any information was accessed or if the affected accounts were compromised in any other way. The breach was reported to law enforcement on Tuesday. The attackers have not yet been identified and the investigation into the incident is still in its early stages.
The vulnerability was remediated Thursday (yesterday) evening. Approximately 50 million accounts have had their access tokens reset and, an additional 40 million accounts have had their access tokens reset as a precautionary step. Today, the 90 million users were prompted to re-login to their Facebook accounts or any other applications that use Facebook login. Once logged in, an explanation of the breach will be available to users at the top of their News Feed.
The “View As” feature has been temporarily disabled for security purposes.
For additional information and information on how you can take immediate action to secure your Facebook account,
please visit: https://newsroom.fb.com/news/2018/09/security-update/


