Spot Weaknesses Before Attackers Do
Hidden vulnerabilities are one of the biggest risks to your firm’s security. Drawbridge Vulnerability Scanning delivers continuous, independent visibility into your IT environment – across networks, endpoints and perimeter systems – so you can identify gaps and prioritize fixes.


Prevention Starts With Visibility
Cyber attackers exploit overlooked weaknesses – from outdated applications to misconfigured firewalls. We help firms demonstrate ongoing vulnerability management, not just point-in-time audits.
Continuously identify and classify vulnerabilities across networks and endpoints
Validate IT hygiene and patching effectiveness
Prioritize remediation based on severity and impact
Provide regulators, boards and investors with proof of proactive risk management
Real-Time Insight. Real-World Protection.
Our service goes beyond static scans. Drawbridge provides continuous monitoring, independent analysis and clear reporting tailored for alternative investment firms.
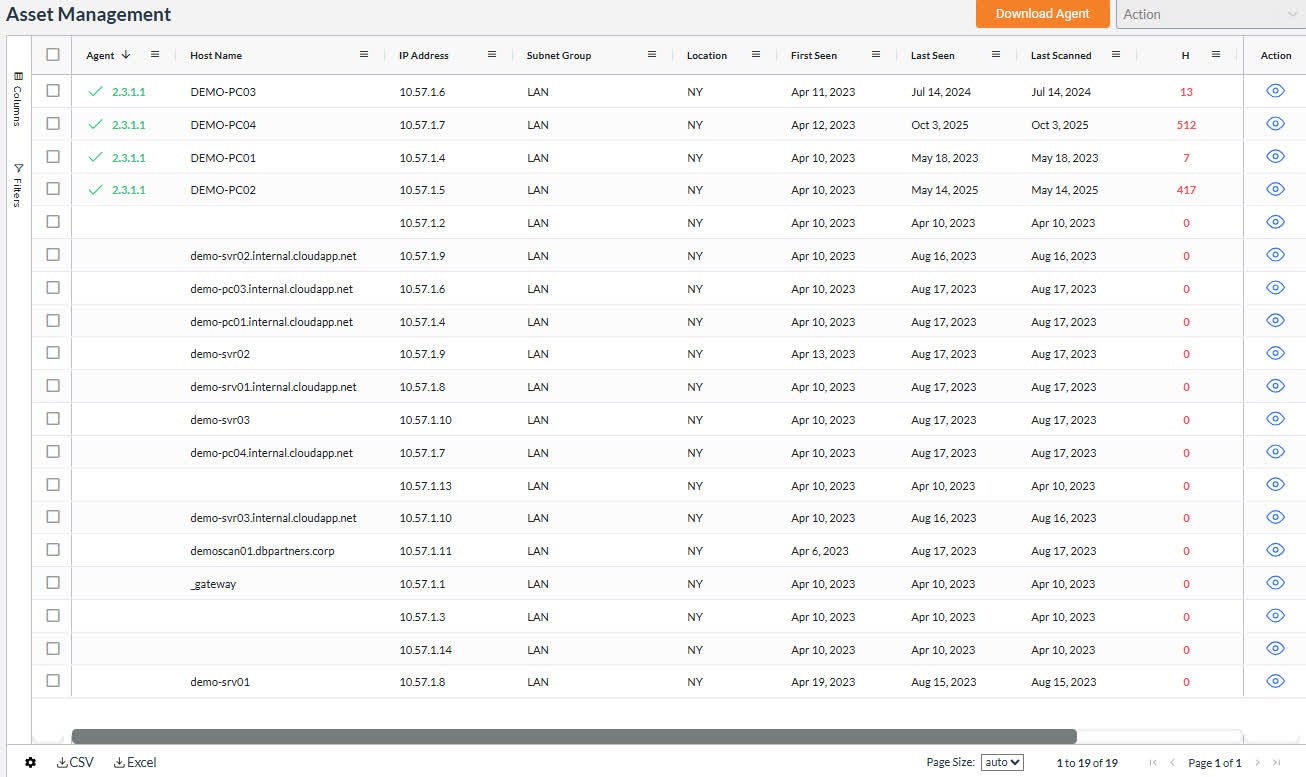
Identify outdated or vulnerable applications on employee devices – wherever they’re located.
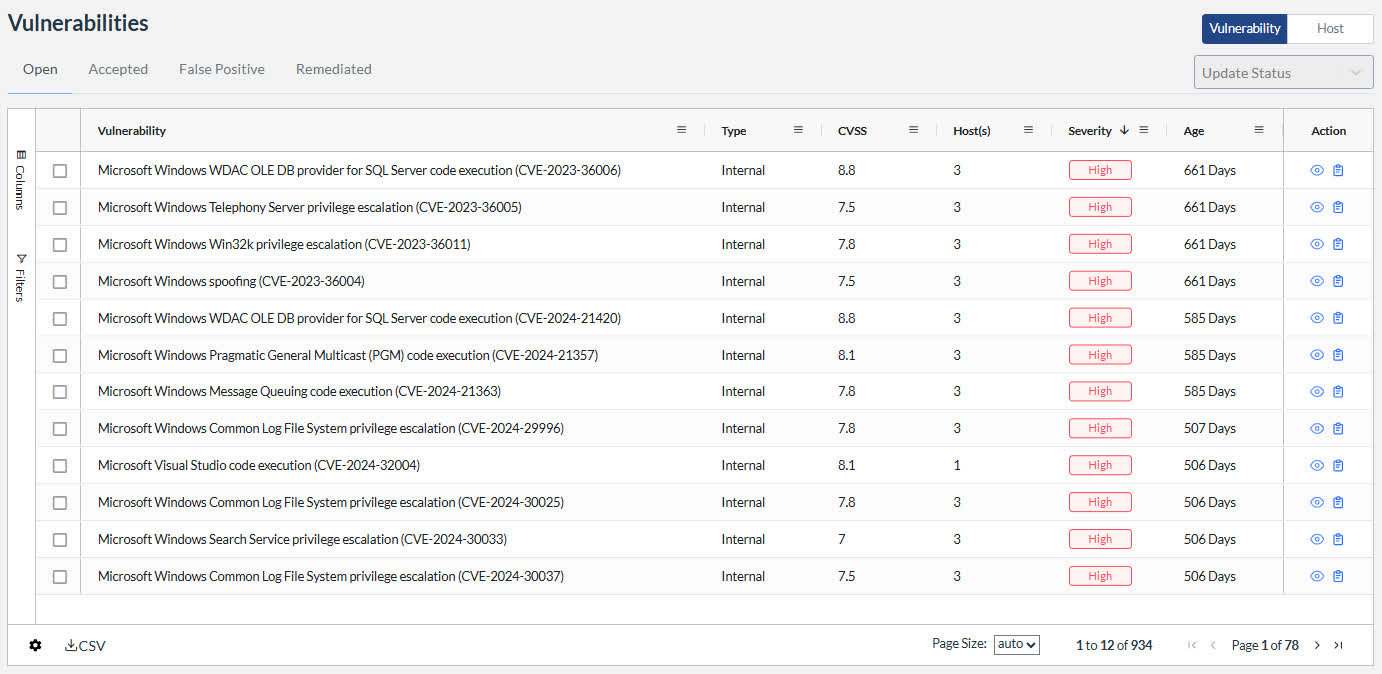
Spot unpatched systems and misconfigurations inside your environment before attackers do.
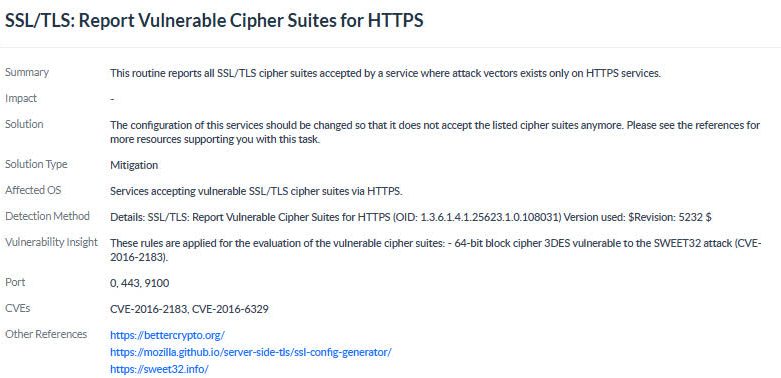
Detect exposed services or open ports on the network edge and close them fast.
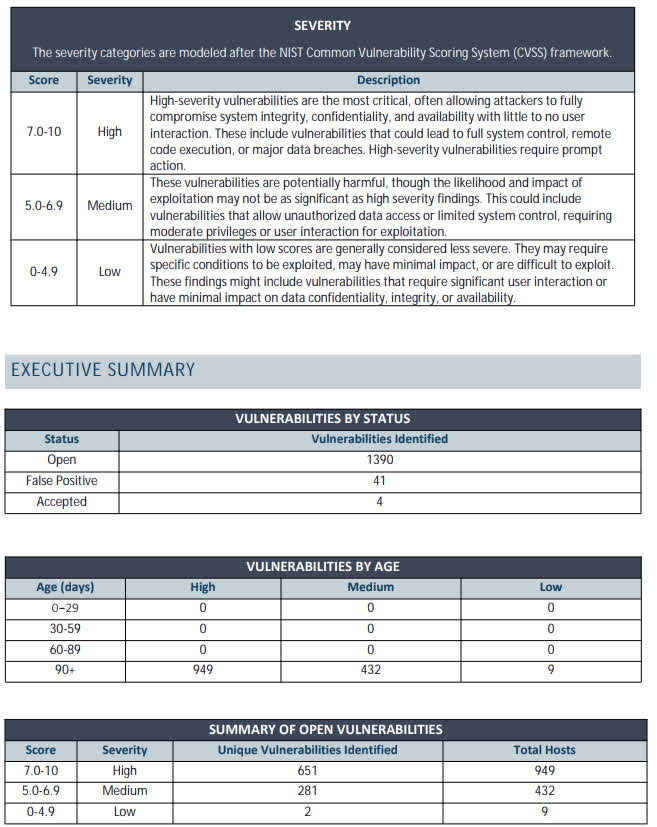
Generate regulator-ready reports proving continuous vulnerability management.
Why Firms Choose Drawbridge for Vulnerability Scanning
Not all scanning is created equal. Drawbridge combines independence, expertise and continuous oversight to deliver results that stand up to investors and regulators.
Continuous Scanning
Real-time updates across networks and endpoints
Independent Findings
Conflict-free validation, unlike MSP-led assessments
Full-Service Deployment
We handle setup, configuration and maintenance with minimal client effort
Alt-Firm Specialization
Purpose-built for hedge funds, private equity and other alternative investments firms

From Findings to Fixes
Trusted by 1,200+ firms to reduce exposure and satisfy regulator expectations.
Whether identifying unpatched servers, flagging vulnerable remote devices or validating SOC/SIEM effectiveness, Drawbridge Scanning gives firms the clarity they need to remediate quickly and reassure stakeholders.